Maybe don’t call Saul? Over 30,000 VoIP devices identifiable worldwide, some with suspected vulnerabilities
Security Affairs
MAY 12, 2021
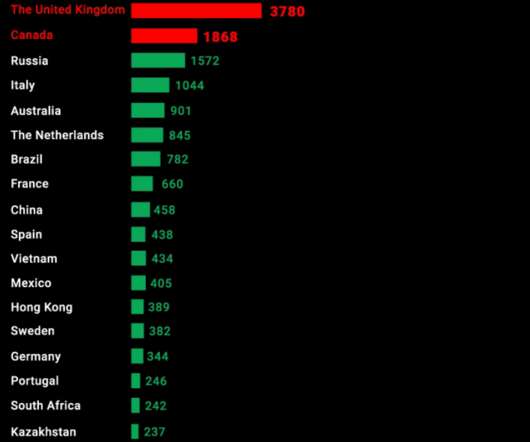
Our research shows that large and small manufacturers are identifiable, with Aastra-Mitel topping the list. Aastra-Mitel tops the manufacturer list, the United States leads the list among countries, and London tops the chart among cities. Devices made by the US manufacturer Polycom, a subsidiary of Plantronics Inc., What we did.











Let's personalize your content