New HiatusRAT campaign targets Taiwan and U.S. military procurement system
Security Affairs
AUGUST 21, 2023
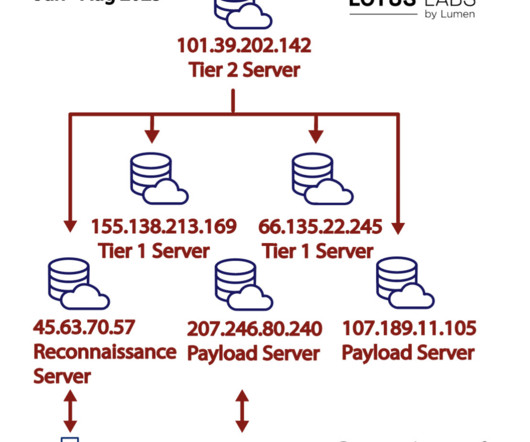
Then they analyzed the connections made to this server to identify potential targets and discovered that over 91% of the inbound connections were from Taiwan, and there appeared to be a preference for Ruckus-manufactured edge devices. military procurement system appeared first on Security Affairs. ” continues the report.


















Let's personalize your content