Phishing campaign targets LATAM e-commerce users with Chaes Malware
Security Affairs
NOVEMBER 18, 2020
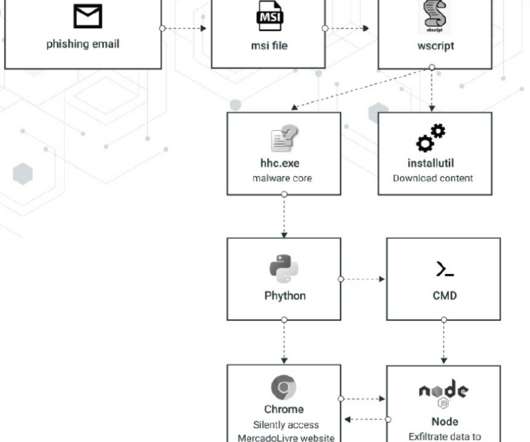
The kill chain starts with phishing messages that use a.docx file that once is opened triggers a template injection attack. bin, researchers also observed the use of a cryptocurrency mining module. . The post Phishing campaign targets LATAM e-commerce users with Chaes Malware appeared first on Security Affairs.












Let's personalize your content