China-linked APT Bronze Starlight deploys ransomware as a smokescreen
Security Affairs
JUNE 26, 2022
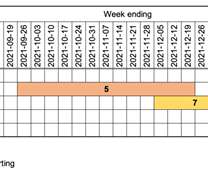
The victims include pharmaceutical companies in Brazil and the U.S., based media organization with offices in China and Hong Kong, electronic component designers and manufacturers in Lithuania and Japan, a law firm in the U.S., and an aerospace and defense division of an Indian conglomerate.













Let's personalize your content