IcedID Malware Revamped With Avoidance Capabilities
Data Breach Today
AUGUST 15, 2020
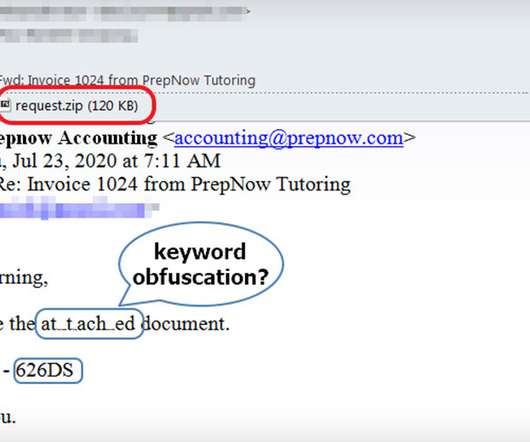
Banking Trojan Has Become More Prevalent Since COVID-19 The IcedID banking Trojan has been updated with additional evasion techniques including a password-protected attachment, keyword obfuscation and a DLL file that acts as a second stage downloader, according to Juniper Threat Labs.















Let's personalize your content