Identity Thieves Bypassed Experian Security to View Credit Reports
Krebs on Security
JANUARY 9, 2023
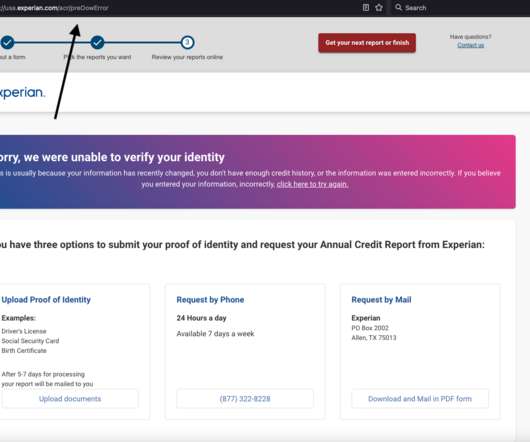
Experian said I had three options for a free credit report at this point: Mail a request along with identity documents, call a phone number for Experian, or upload proof of identity via the website. For example, there were four phone numbers on my Experian credit file: Only one of them was mine, and that one hasn’t been mine for ages.











Let's personalize your content