Using Microsoft Powerpoint as Malware Dropper
Security Affairs
NOVEMBER 16, 2018
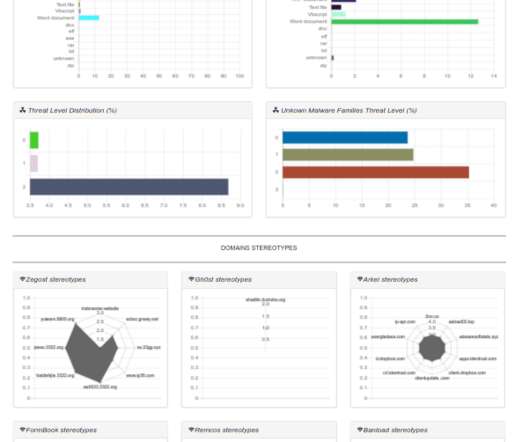
Marco Ramilli, founder and CEO at cyber security firm Yoroi has explained how to use Microsoft Powerpoint as Malware Dropper. Nowadays Microsoft office documents are often used to propagate Malware acting like dynamic droppers. I am a computer security scientist with an intensive hacking background.










Let's personalize your content