Kr00k Wi-Fi Encryption flaw affects more than a billion devices
Security Affairs
FEBRUARY 26, 2020
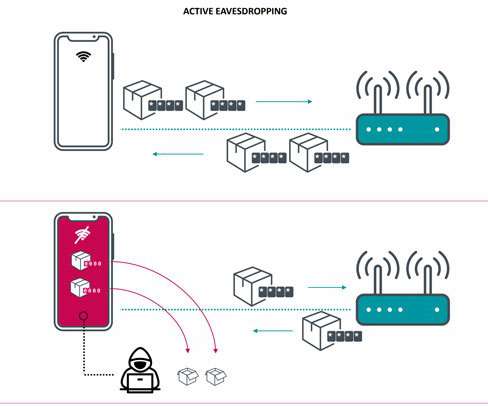
A high-severity hardware vulnerability, dubbed Kr00k , in Wi-Fi chips manufactured by Broadcom and Cypress expose over a billion devices to hack. Cybersecurity researchers from ESET have discovered a new high-severity hardware vulnerability, dubbed Kr00k , that affects Wi-Fi chips manufactured by Broadcom and Cypress.













Let's personalize your content