New Pro-Ocean crypto-miner targets Apache ActiveMQ, Oracle WebLogic, and Redis installs
Security Affairs
JANUARY 31, 2021
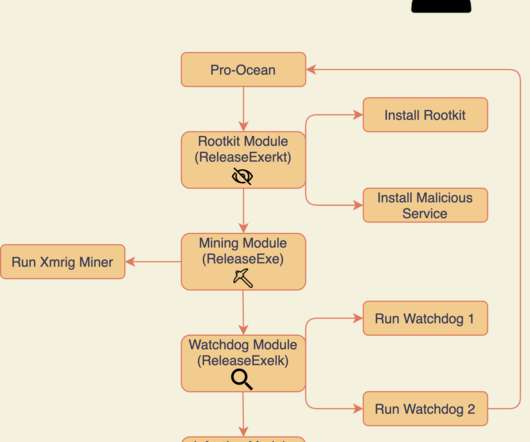
The new malware implement new and improved rootkit and worm capabilities, it continues to target cloud applications by exploiting known vulnerabilities such as Oracle WebLogic ( CVE-2017-10271 ) and Apache ActiveMQ ( CVE-2016-3088 ) servers. “Pro-Ocean uses known vulnerabilities to target cloud applications.










Let's personalize your content