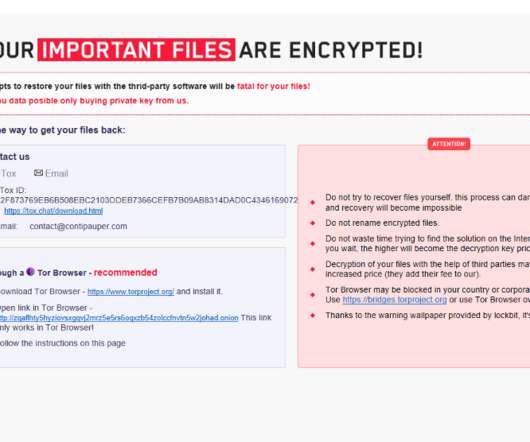
LockFile Ransomware uses a new intermittent encryption technique
Security Affairs
AUGUST 31, 2021
Recently emerged LockFile ransomware family LockFile leverages a novel technique called intermittent encryption to speed up encryption. Sophos researchers discovered that the group is now leveraging a new technique called “intermittent encryption” to speed up the encryption process.











Let's personalize your content