New RA Group ransomware gang is the latest group using leaked Babuk source code
Security Affairs
MAY 15, 2023
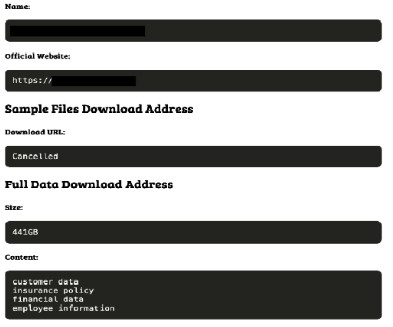
Compromised organizations operate in different business verticals, including manufacturing, wealth management, insurance providers, and pharmaceuticals. The ransomware supports intermittent encryption to speed up the encryption process. GAGUP” to the name of the encrypted files. .”













Let's personalize your content