RedFoxtrot operations linked to China’s PLA Unit 69010 due to bad opsec
Security Affairs
JUNE 19, 2021
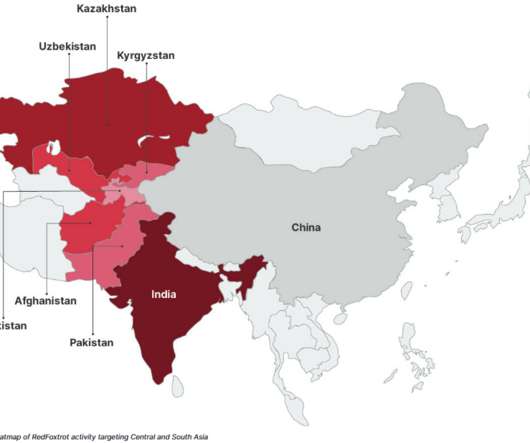
Experts attribute a series of cyber-espionage campaigns dating back to 2014, and focused on gathering military intelligence, to China-linked Unit 69010. These targets suggest the group is likely interested in gathering intelligence on military technology and defense” reads the report published by the Insikt Group. .




















Let's personalize your content