New LockFile ransomware gang uses ProxyShell and PetitPotam exploits
Security Affairs
AUGUST 21, 2021
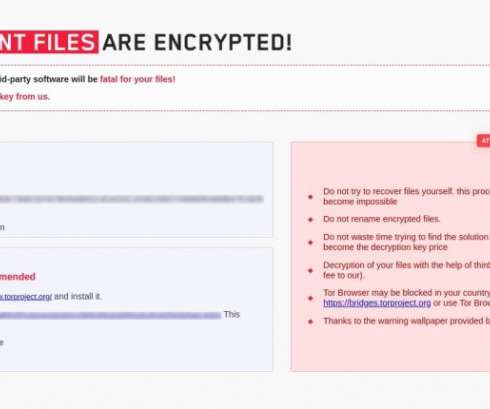
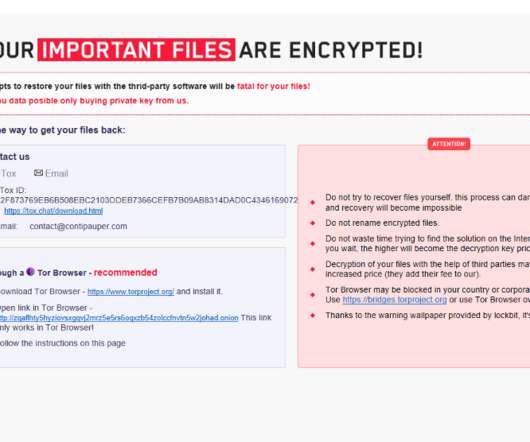
The popular security expert Kevin Beaumont was one of the first researchers to report that the LockFile operators are using the Microsoft Exchange ProxyShell and the Windows PetitPotam vulnerabilities to take over Windows domains. financial organization on July 20, 2021, with its latest activity seen as recently as August 20.









Let's personalize your content