Targeted operation against Ukraine exploited 7-year-old MS Office bug
Security Affairs
APRIL 28, 2024
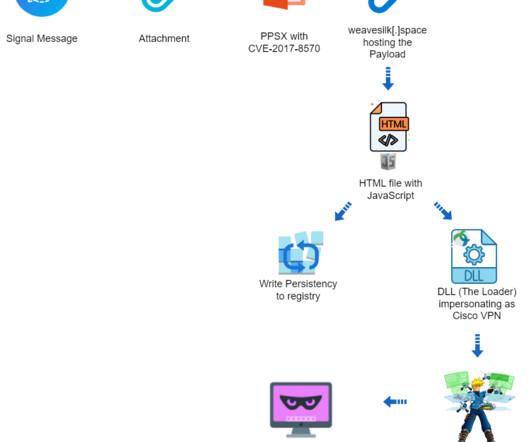
It’s a PPSX file, seemingly an outdated US Army manual for tank mine clearing blades (MCB). The researchers pointed out that the use of the “script:” prefix demonstrates the exploitation of the vulnerability CVE-2017-8570 , a bypass for CVE-2017-0199. The remote script, named “widget_iframe.617766616773726468746672726a6834.html,”














Let's personalize your content