Chinese cyberspies used a new PlugX variant, dubbed THOR, in attacks against MS Exchange Servers
Security Affairs
JULY 28, 2021
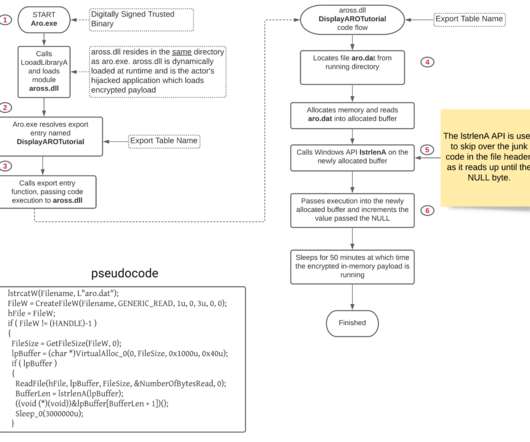
In the attacks investigated by Palo Alto Networks, the APT group leveraged legitimate executables such as BITSAdmin to download an innocuous file named Aro.dat from a GitHub repository under the control of the threat actors. The analysis of the file revealed that it includes the encrypted and compressed PlugX payload.












Let's personalize your content