NK-linked InkySquid APT leverages IE exploits in recent attacks
Security Affairs
AUGUST 18, 2021
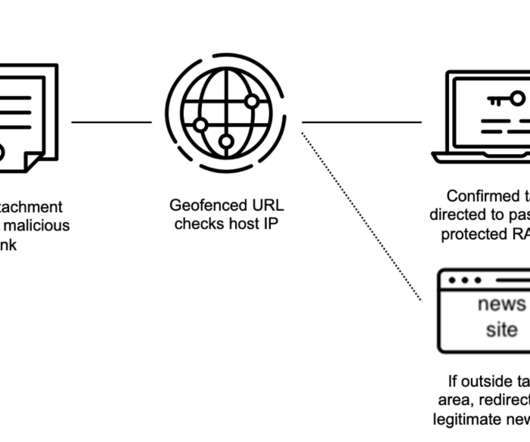
APT37 has been active since at least 2012, it mainly targeted government, defense, military, and media organizations in South Korea. Harvest cookies and a password database for supported browsers. Spawn a thread to recursively search a path and upload files as a ZIP archive. ” reads the post published by Volexity.











Let's personalize your content