NK-linked InkySquid APT leverages IE exploits in recent attacks
Security Affairs
AUGUST 18, 2021
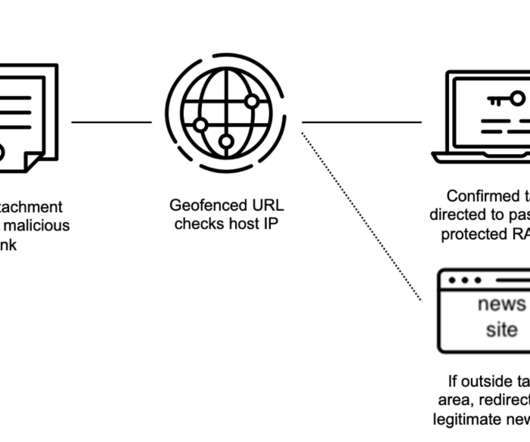
APT37 has been active since at least 2012, it mainly targeted government, defense, military, and media organizations in South Korea. Spawn a thread to recursively search a path and upload files as a ZIP archive. The watering hole attacks on the Daily NK was conducted from March 2021 until early June 2021. services. .











Let's personalize your content