China-linked Budworm APT returns to target a US entity
Security Affairs
OCTOBER 13, 2022
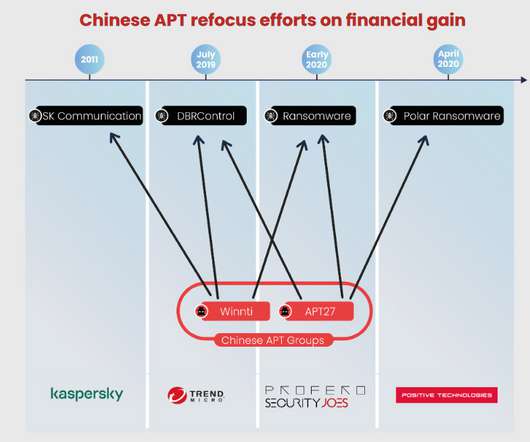
The China-linked APT27 group has been active since 2010, it targeted organizations worldwide, including U.S. defense contractors , financial services firms, and a national data center in Central Asia. It is designed to load malicious DLLs and encrypt payloads.” based organization. Pierluigi Paganini.














Let's personalize your content