Black Basta Ransomware gang accumulated at least $107 million in Bitcoin ransom payments since early 2022
Security Affairs
DECEMBER 1, 2023
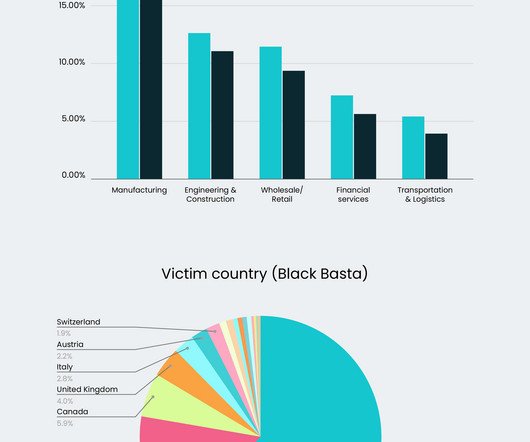
” Most of the victims are in the manufacturing, engineering and construction, and retail sectors. Qakbot , also known as QBot, QuackBot and Pinkslipbot, is an info-stealing malware that has been active since 2008. The largest received ransom payment was $9 million, and at least 18 of the ransoms exceeded $1 million.












Let's personalize your content