REMnux Tools List for Malware Analysis
Lenny Zeltser
OCTOBER 13, 2020
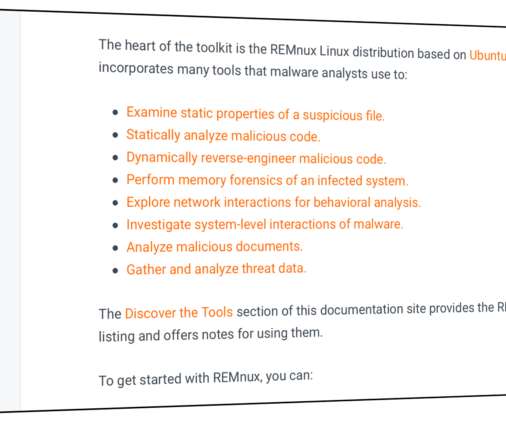
To guide you through the process of examining malware, REMnux documentation lists the installed tools by category. In addition to providing numerous tools as part of the REMnux distro, the project also offers several malware analysis tools as Docker images.














Let's personalize your content