QR Codes: A Growing Security Problem
eSecurity Planet
FEBRUARY 21, 2022
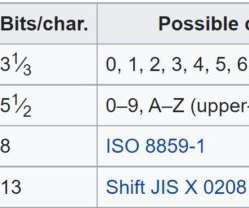
Here’s how QR codes work, how hackers can use them against you, and how to defend yourself and your organization. How QR Codes Work Behind the Scenes. Also read: How to Defend Common IT Security Vulnerabilities. Flawed Implementations Can Be Devastating.















Let's personalize your content