Xenomorph malware is back after months of hiatus and expands the list of targets
Security Affairs
SEPTEMBER 26, 2023
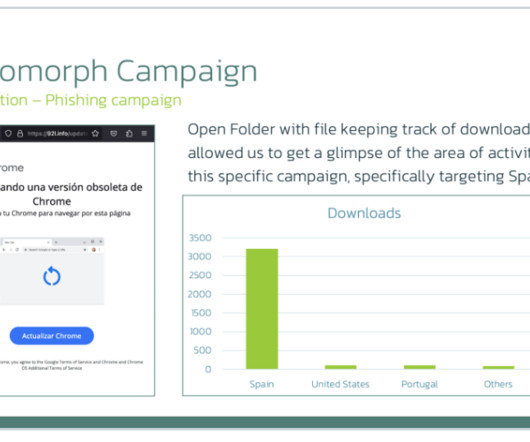
The analysis of the code revealed the presence of not implemented features and the large amount of logging present, a circumstance that suggests that this threat is under active development. This allowed the researchers to monitor the server, identifying multiple interesting files. Most of the downloads were from Spain. .












Let's personalize your content