BlackCat Adds Brute Ratel Pentest Tool to Attack Arsenal
Data Breach Today
JULY 16, 2022
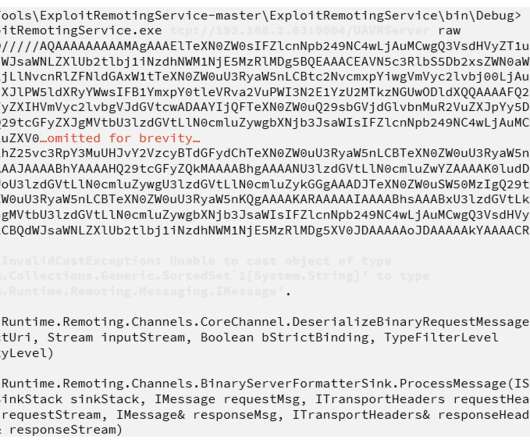
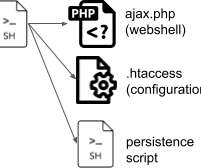
Gang Targets Large Corporations Across the U.S., Europe and Asia The cybercriminals behind BlackCat ransomware have upgraded their arsenal by adding Brute Ratel, a pentesting tool with remote access features that are used by attackers. The group targets large corporations in different industry segments across the U.S., Europe and Asia.













Let's personalize your content