Dark Basin, a hack-for-hire group that remained under the radar for 7 years
Security Affairs
JUNE 11, 2020
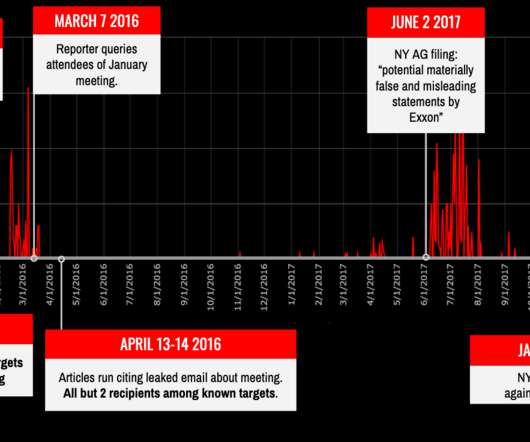
Researchers from Citizen Lab uncovered the operations of a hack-for-hire group tracked as Dark Basin that targeted thousands of journalists, elected and senior government officials, advocacy groups, and hedge funds worldwide over 7 years. ” reads the report published by Citizen Lab. ” reads the report published by Citizen Lab.















Let's personalize your content