New Go-based Redigo malware targets Redis servers
Security Affairs
DECEMBER 1, 2022
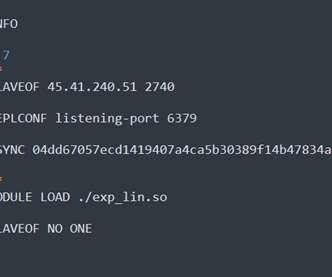
The attack chain starts with scans for the Redis server exposing port 6379 to the internet, then threat actors attempt to connect and run the following Redis commands: INFO command – this command allows adversaries to receive information about our Redis server. Attackers loads the library file exp_lin.so to the disk of the replica.









Let's personalize your content