New Go-based Redigo malware targets Redis servers
Security Affairs
DECEMBER 1, 2022
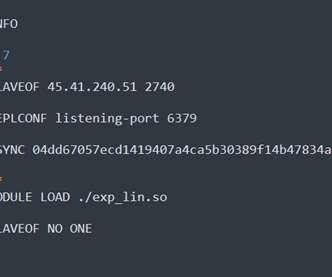
Among the data they receive, they now know which server’s version is vulnerable to CVE-2022-0543 (As we explained earlier, the honeypot was built with this vulnerability on purpose). The attacking server that is defined as the master uses this connection to download the shared library exp_lin.so to the disk of the replica.











Let's personalize your content