Magecart attacks are still around but are more difficult to detect
Security Affairs
JUNE 22, 2022
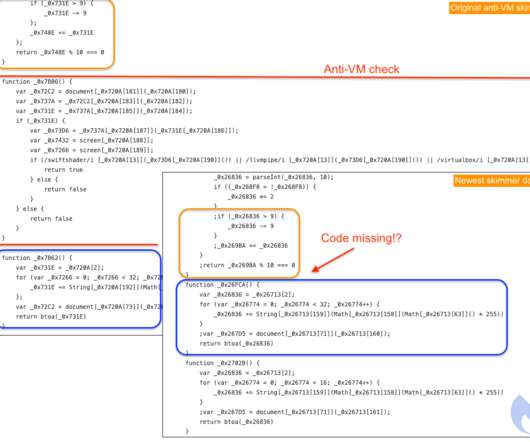
Malwarebytes researchers observed the use of 3 different themes by the threat actor to hide their skimmer, named after JavaScript libraries: hal-data[.]org/gre/code.js The researchers explained that they have generally seen less skimming attacks during the past several months, perhaps because they were more focused on the Magento CMS.











Let's personalize your content