UNC2529, a new sophisticated cybercrime gang that targets U.S. orgs with 3 malware
Security Affairs
MAY 5, 2021
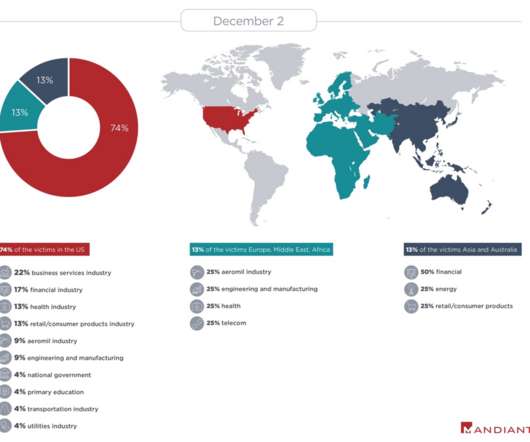
.” At the time of the report, although Mandiant has no evidence about the purposes of the attacks, the broad targeting across multiple industries and the choosing of targets of a global scale, suggests that the attackers could be financially motivated. orgs with 3 malware appeared first on Security Affairs. Pierluigi Paganini.











Let's personalize your content