EventBot, a new Android mobile targets financial institutions across Europe
Security Affairs
APRIL 30, 2020
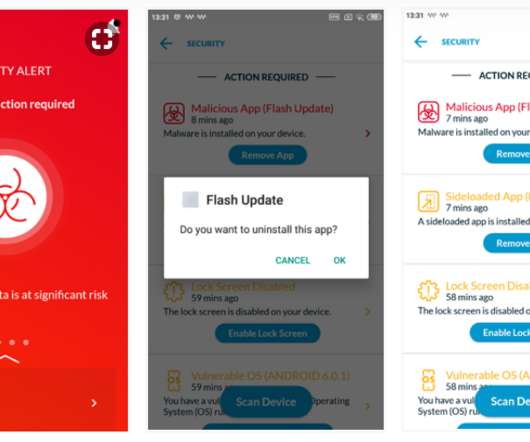
Security experts from Cybereason Nocturnus team discovered a new piece of Android malware dubbed EventBot that targets banks, financial services across Europe. Researchers from Cybereason Nocturnus team discovered a new piece of Android malware dubbed EventBot that targets banks, financial services across Europe.

















Let's personalize your content