China-linked APT BlackTech was spotted hiding in Cisco router firmware
Security Affairs
SEPTEMBER 27, 2023
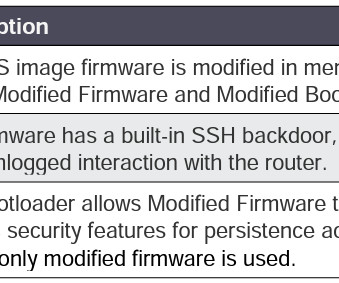
US and Japanese intelligence, law enforcement and cybersecurity agencies warn of a China-linked APT, tracked as BlackTech (aka Palmerworm, Temp.Overboard, Circuit Panda, and Radio Panda), that planted backdoor in Cisco router firmware to access multinational companies’ networks. ” reads the joint advisory.










Let's personalize your content