Nation-state actors exploited two zero-days in ASA and FTD firewalls to breach government networks
Security Affairs
APRIL 24, 2024
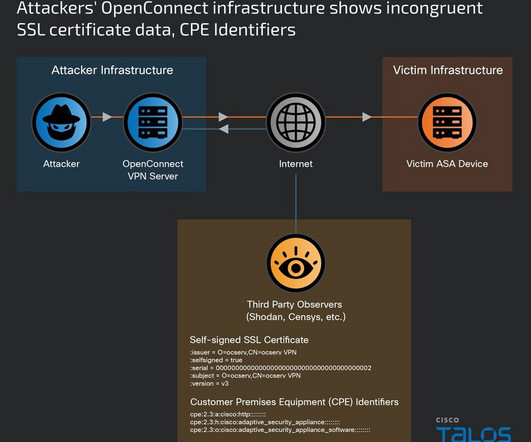
Nation-state actor UAT4356 has been exploiting two zero-days in ASA and FTD firewalls since November 2023 to breach government networks. Early in 2024, a customer contacted Cisco to report a suspicious related to its Cisco Adaptive Security Appliances (ASA). Cisco Talos researchers tracked this cyber-espionage campaign as ArcaneDoor.













Let's personalize your content