No, I Did Not Hack Your MS Exchange Server
Krebs on Security
MARCH 28, 2021
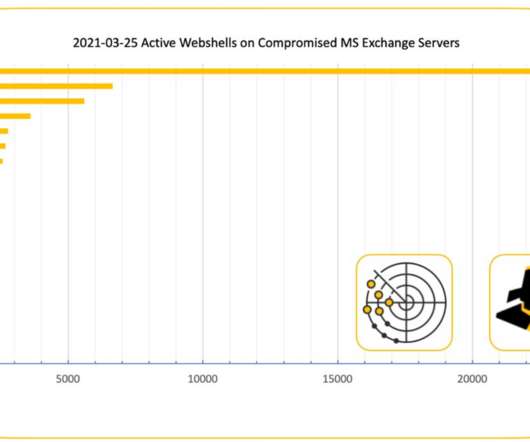
The group looks for attacks on Exchange systems using a combination of active Internet scans and “honeypots” — systems left vulnerable to attack so that defenders can study what attackers are doing to the devices and how. “We have been testing 367 known web shell paths via scanning of Exchange servers.”










Let's personalize your content