Gootkit delivery platform Gootloader used to deliver additional payloads
Security Affairs
MARCH 1, 2021
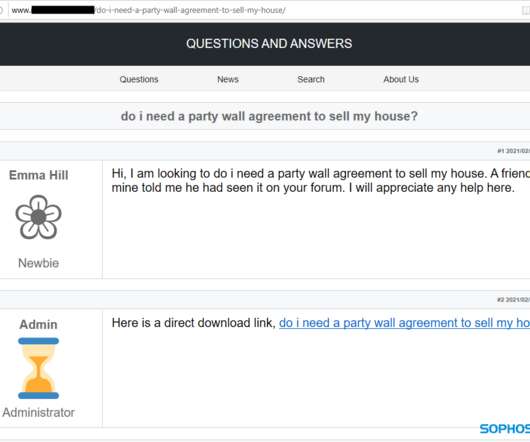
In its latest attempts to evade detection by endpoint security tools, Gootloader has moved as much of its infection infrastructure to a “fileless” methodology as possible.” file is the initial infector, and the only stage of the infection at which a malicious file is written to the filesystem. “This.js










Let's personalize your content