Gootkit delivery platform Gootloader used to deliver additional payloads
Security Affairs
MARCH 1, 2021
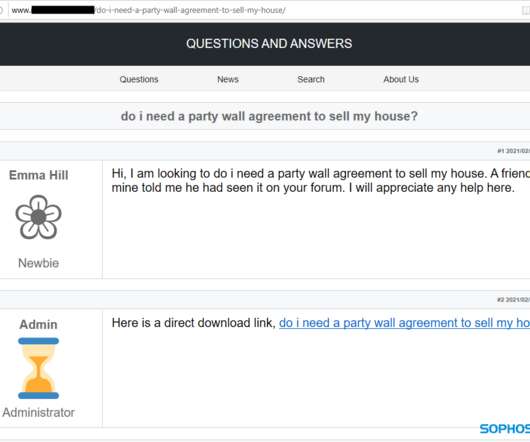
When the visitor clicks on the link provided by the search engine, they are redirected to landing pages that answer their exact questions, using the same wording as the search query. file is the initial infector, and the only stage of the infection at which a malicious file is written to the filesystem.










Let's personalize your content