Operation Cronos: law enforcement disrupted the LockBit operation
Security Affairs
FEBRUARY 19, 2024
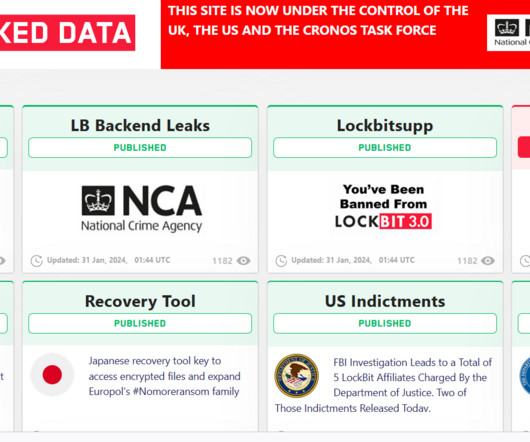
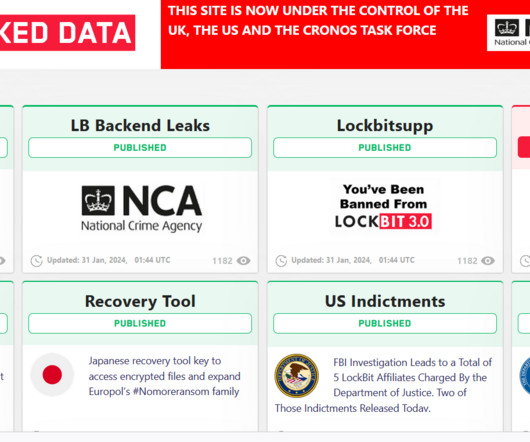
A joint law enforcement action, code-named Operation Cronos, conducted by law enforcement agencies from 11 countries has disrupted the LockBit ransomware operation. In 2022, LockBit was one of the most active ransomware groups, and its prevalence continued into 2023. “The site is now under the control of law enforcement. .











Let's personalize your content