A new piece of Snake Ransomware targets ICS processes
Security Affairs
JANUARY 28, 2020
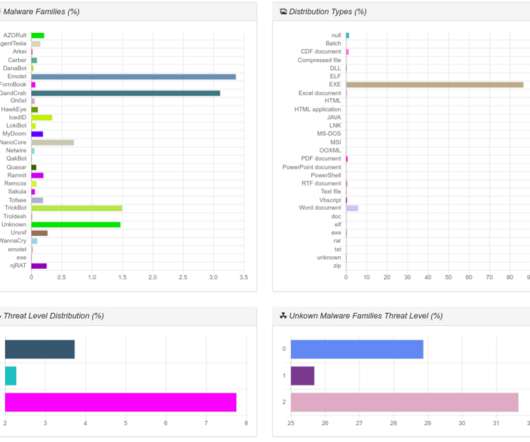
Like other ransomware, upon execution Snake will remove the computer’s Shadow Volume Copies, it also kills numerous processes related to SCADA systems, virtual machines, industrial control systems, remote management tools, network management software, and more. a file named invoice.doc is encrypted and renamed like invoice.docIksrt.









Let's personalize your content