Youtube Scammers Made $1.6 million in Fake Crypto Giveaway
Data Breach Today
APRIL 9, 2022
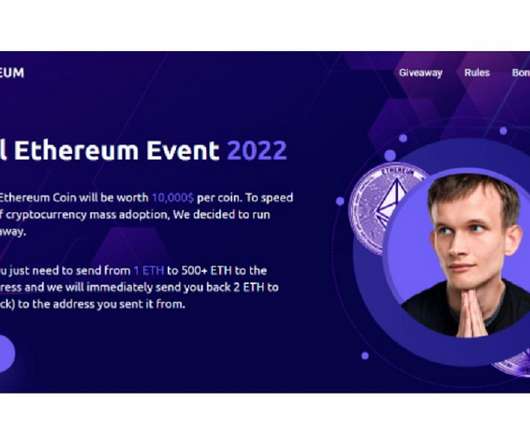
Scammers Exploited YouTube Streams Attracting Over 165,000 Viewers A group of fraudsters made more than $1.6 million in a massive scam using fake cryptocurrency giveaway YouTube streams attracting more than 165,000 viewers. The campaign also exploited the names of Vitalik Buterin, Elon Musk, Michael Saylor and other crypto enthusiasts.












Let's personalize your content