Balikbayan Foxes group spoofs Philippine gov to spread RATs
Security Affairs
NOVEMBER 1, 2021
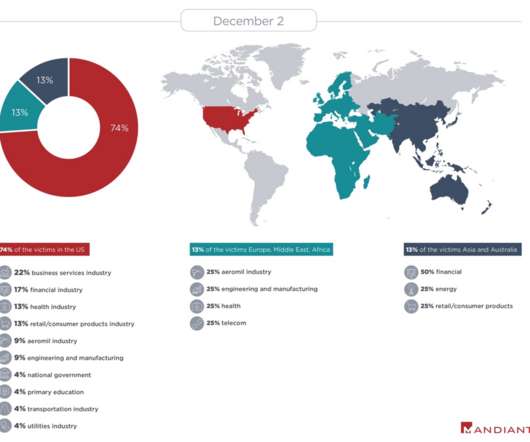
Experts uncovered a new threat actor, tracked as Balikbayan Foxes, that is impersonating the Philippine government to spread malware. . The group focuses on Shipping/Logistics, Manufacturing, Business Services, Pharmaceutical, and Energy entities, among others. ” reads the analysis published by the experts. .












Let's personalize your content