Cybersecurity agencies published a joint LockBit ransomware advisory
Security Affairs
JUNE 15, 2023
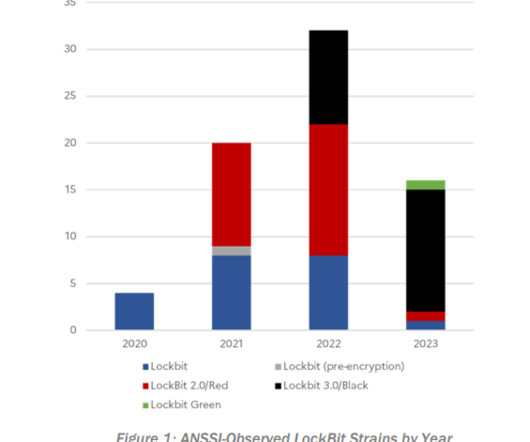
Help us #StopRansomware by visiting [link] pic.twitter.com/G5jpxtB0Fw — Cybersecurity and Infrastructure Security Agency (@CISAgov) June 14, 2023 The LockBit ransomware operation was the most active in 2022 and according to the researchers it is one of the most prolific RaaS in 2023. law enforcement). was the prevalent variant in 2023.



















Let's personalize your content