North Korea-linked Lazarus APT targets the COVID-19 research
Security Affairs
DECEMBER 25, 2020
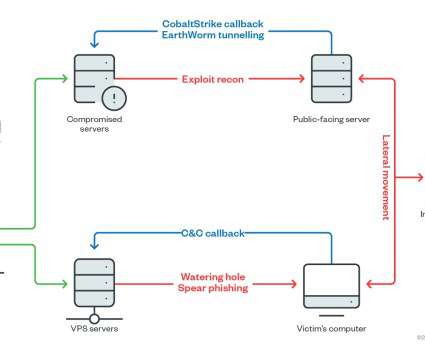
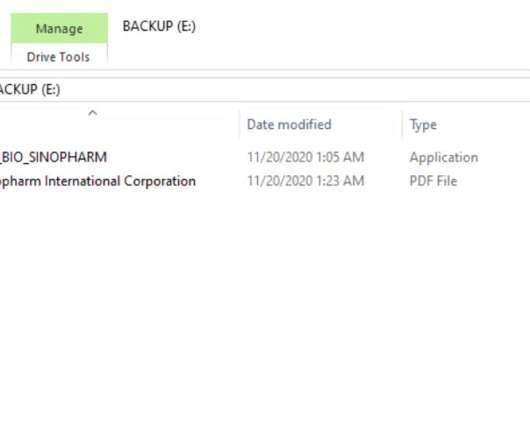
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. The attacks aimed at a Ministry of Health and a pharmaceutical company involved in the development of the COVID-19 vaccine.








Let's personalize your content