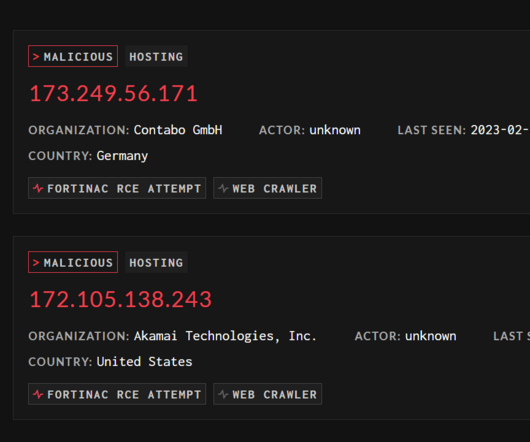
Fortinet FortiNAC CVE-2022-39952 flaw exploited in the wild hours after the release of PoC exploit
Security Affairs
FEBRUARY 23, 2023
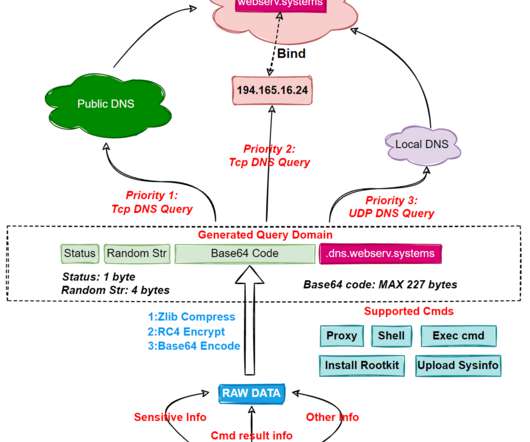
The two vulnerabilities, tracked as CVE-2022-39952 and CVE-2021-42756 , are respectively an external control of file name or path in Fortinet FortiNAC and a collection of stack-based buffer overflow issues in the proxy daemon of FortiWeb. is an external control of file name or path in the keyUpload scriptlet of FortiNAC.










Let's personalize your content