HTML Smuggling Techniques on the Rise: Microsoft
eSecurity Planet
NOVEMBER 16, 2021
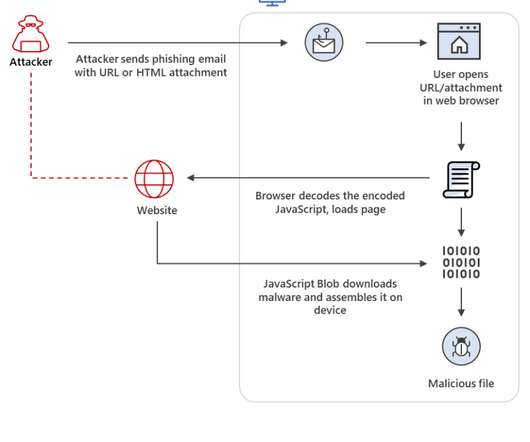
“This technique is highly evasive because it could bypass standard perimeter security controls, such as web proxies and email gateways, that often only check for suspicious attachments (for example, EXE, ZIP, or DOCX) or traffic based on signatures and patterns,” they wrote. Therefore, HTML smuggling is quite effective here.”.











Let's personalize your content