US GOV OFFERS A REWARD OF UP TO $15M FOR INFO ON LOCKBIT GANG MEMBERS AND AFFILIATES
Security Affairs
FEBRUARY 21, 2024
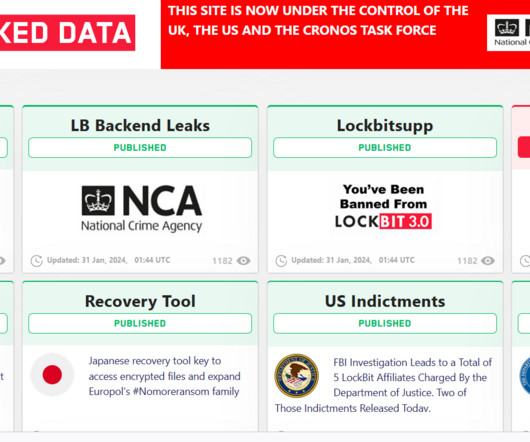
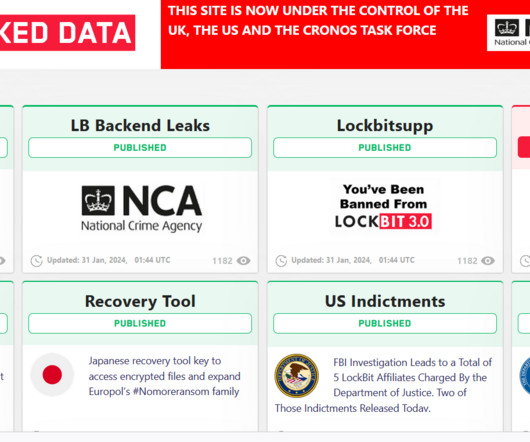
The NCA will reach out to victims based in the UK in the coming days and weeks, providing support to help them recover encrypted data. Today, additional criminal charges against Kondratyev were unsealed in the Northern District of California related to his deployment in 2020 of ransomware against a victim located in California.”













Let's personalize your content