Why Humans Alone Can't Beat Cybercrime
Data Breach Today
MAY 7, 2023
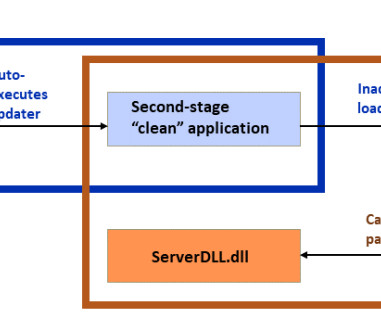
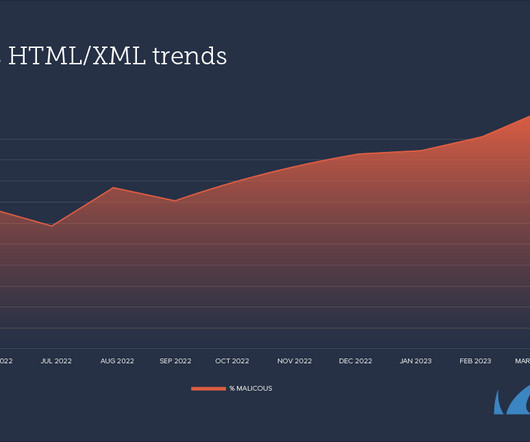
Rubrik CEO Sinha on Why Defenders Need Latest Tech to Keep Up With Threat Actors Cybercrime has grown considerably in the last several years. The scope, velocity and variability of attacks have increased, as has the attack surface - and it's impossible for humans alone to understand, correlate, find the cause, analyze and fix it, said Bipul Sinha, co-founder and CEO of Rubrik.














Let's personalize your content