Cyber Threats Observatory Gets Improvements
Security Affairs
MAY 3, 2020
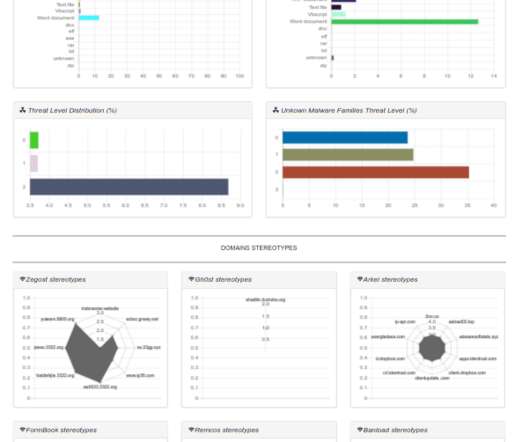
In other words, it could be nice to see what are the patterns used by malware in both: domain names, file names and process names. TOP domains, TOP processes and TOP File Names. I am a computer security scientist with an intensive hacking background. About the author: Marco Ramilli, Founder of Yoroi.










Let's personalize your content