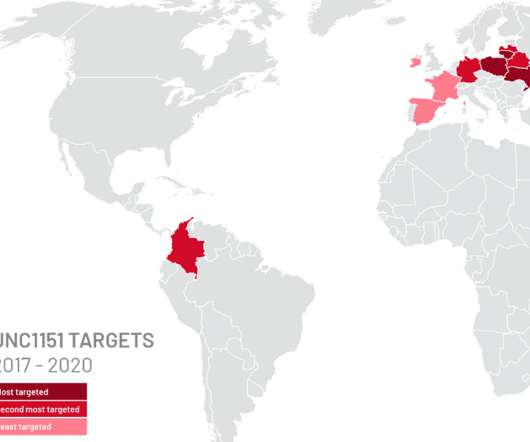
Ukraine: Belarusian APT group UNC1151 targets military personnel with spear phishing
Security Affairs
FEBRUARY 25, 2022
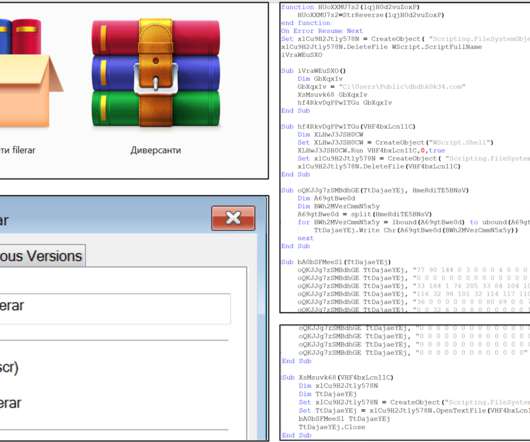
The Ukrainian agency attributes the campaign to the Belarus-linked cyberespionage group tracked as UNC1151. In mid-January, the government of Kyiv attributed the defacement of tens of Ukrainian government websites to Belarusian APT group UNC1151. Attackers spear-phishing messages have been sent from email accounts using the domains i[.]ua-passport[.]space













Let's personalize your content