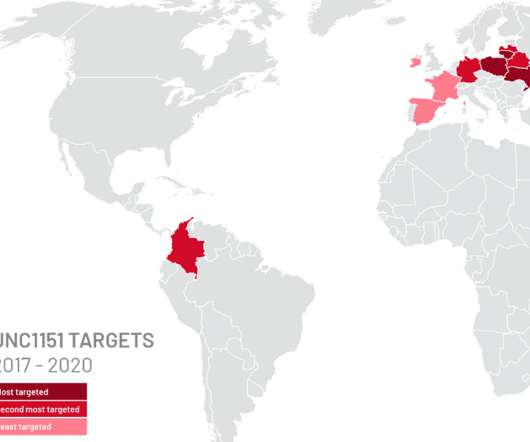
Ukraine: Belarusian APT group UNC1151 targets military personnel with spear phishing
Security Affairs
FEBRUARY 25, 2022
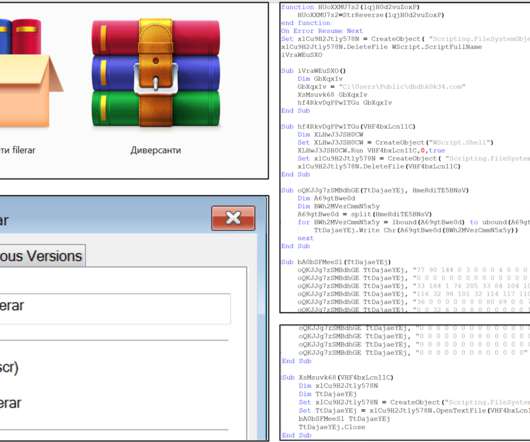
In mid-January, the government of Kyiv attributed the defacement of tens of Ukrainian government websites to Belarusian APT group UNC1151. In November 2021, Mandiant Threat Intelligence researchers linked the Ghostwriter disinformation campaign (aka UNC1151) to the government of Belarus. reads a translation of the message.














Let's personalize your content